Is nothing safe?
Spy Craft
It sounds like a scene from a spy thriller movie: hackers recover the encrypted keys to a locked room by analyzing the glow from the power LED on the device storing them.
This may sound like a too-cool to-be-real plot point, but a team of researchers recently published a method that purports to successfully perform this ingenious hack. This method is a form of side-channel attack, which exploits information gleaned from a fundamental or physical characteristic of a system, inadvertently leaking information to hackers.
Characteristics that could be exploited include power consumption, sound patterns, electromagnetic properties, and timing. In the case of this study, by researchers from Cornell University and Ben-Gurion University of the Negev, the team analyzed the brightness and color of a device's power light.
Light Bulb Moment
A CPU making cryptographic computations changes a device's power consumption, according to the researchers, and this shows up by impacting the brightness and color of the device's LED.
Footage of those faint oscillations, the researchers claim, can be processed and analyzed by hackers to precisely determine the encrypted keys, a method the paper's co-authors called video-based cryptanalysis.
We're In
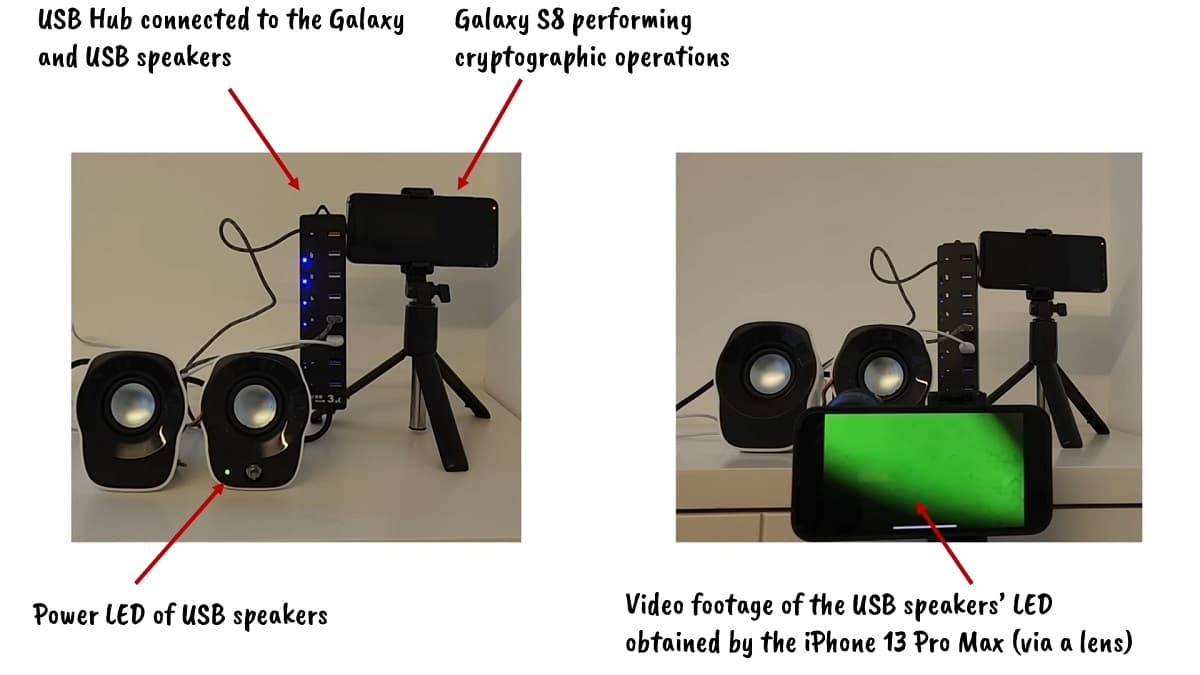
In experiments, the team showed the effectiveness of the method. In one, they say they were able to hijack an Internet-connected security cam and capture footage of the power LED of a smart card reader 16 meters away. After processing and analyzing the footage, the team was able to recover the 256-bit key.
In another study, they were able to take iPhone footage of the power LED of Logitech speakers that were hooked up to an USB hub that was also charging a Samsung Galaxy S8 smart phone. From looking at the speakers' power LED and analyzing its colors and brightness, the team says they were able to uncover the 378-bit key for the Samsung Galaxy — a remarkable scenario because the key was solved indirectly by looking at another connected device.
"It’s not intrusive, and you can use common or popular devices such as a smartphone in order to apply the attack," said lead researcher Ben Nassi in an interview with Ars Technica. "For the case of the Internet-connected video camera, you don’t even need to approach the physical scene in order to apply the attack."
More on encryption: Cryptographers Furious That “Crypto” Now Means Something Else
Share This Article